Cross-site Scripting (XSS) - DOM (CWE-79)
Description
DOM (Document Object Model) is model which treats HTML and XML document as Tree structure.
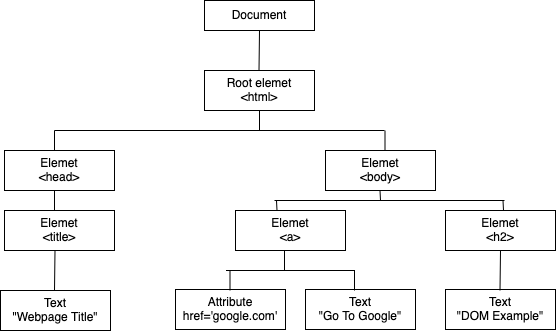
DOM Based XSS is different form Stored and reflected XSS. In both stored and reflected XSS, Malicious javascript is going in the request, and reflecting from the server and web application is Dynamic. But in DOM-based XSS, It is not the case.
DOM Based XSS occurs when the Application takes user-input and uses the same to modify DOM.
Example 1
Let's say; Website has a welcome page, which has URL as below,
https://www.site.com/welcome.html?user=Rahul
This is a static webpage, which rendered as,
Welcome Rahul
So, if you change URL to
https://www.site.com/welcome.html?user=Anything
the webpage will be changed to
Welcome Anything
And this is done using, javascript innerHTML function.
So, Attaceker can add malicious script into URL, as
https://www.site.com/welcome.html?user=Rahul<script>alert('DOM XSS')</script>
Example 2
Consider a simple webpage, which can do basic mathematic operations like addition, subtraction, multiplication.
<!DOCTYPE html>
<html>
<head><title>DOM XSS : Simple Math Calculator</title></head>
<body>
<p id="result"></p>
<script>
var solve = document.URL.split("solve=")[1];
document.getElementById('result').innerHTML = eval(solve);
</script>
</body>
</html>
When, user visit,
https://www.site.com/math.html?solve=1+4
Webpage will display result, as 5
So, if you change URL to
https://www.site.com/math.html?solve=8*7
it will give,
56
So, Attacker can add a malicious script into URL, as
https://www.site.com/math.html?solve=AnyMaliciousJavaScriptHere
Whatever you give to solve= as a GET parameter is the same as given to Javascript eval() function, which is dangerous here.
Impact
Impact of DOM-based XSS will be same as Reflected XSS.
Prevention
- Avoid user given data for DOM Modification or redirection.
- Strict Filters should be applied to user input based on expected input.
- Prevention methods of Stored/reflected XSS should be considered for preventing DOM-based XSS also, but in client-side code.