No Rate Limiting on SMS-Triggering
Description
The website can have SMS-Triggering End Point, which means SMS will be sent to a given mobile number by the web application with some pre-defined or dynamic content.
If there is no Rate Limiting on such functionality, An attacker can misuse it to do SMS bombing
SMS bombing means sending a large number of duplicate SMS to the same mobile number.
Example
for an e.g., the website may have SEND OTP functionality either on Register/login page or forgot password page.
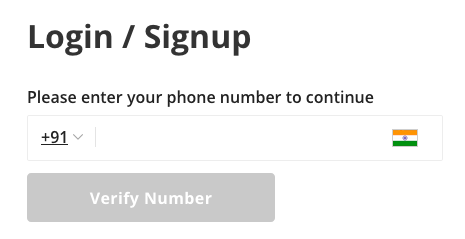 when user fill his mobile number and click on submit button, the user will get SMS from that website, like
when user fill his mobile number and click on submit button, the user will get SMS from that website, like
Your OTP is 1234. Do not share it with anyone.
An attacker can misuse this and send large number of SMS to victim within small amount of time. Due to such SMS bombing victim may miss some important sms like bank transaction alert in between these duplicate messages.
Impact
- An attacker can put the victim in trouble by SMS bombing.
- Wastage of resources.
- Websites use 3rd party SMS API Services (), which costs per SMS. So there will be a financial loss.
Prevention
- Implement rate-limiting in your application based on source IP as well as active session.
- Block that IP / Session if you are getting multiple requests even after sending
429 Too Many Requestsresponse.