Username/Email Enumeration
Overview
this is intro part
Description
** Enumeration** is a vulnerability in web applications which allow an attacker to guess and confirm email/username of the registered user. It will increase the attack surface. An attacker can use these usernames/emails further to account for Takeover.
Types of Enumeration:
-
Brute Force based
- The attacker has to Bruteforce on some end-point to check the weather that email/user is existing or not.
- Attackers use a dictionary of popular usernames and enumerate it.
- This kind of Enumeration can be blocked by Rate limiting or by enabling Captcha.
-
Non-Brute Force based (Dumpable Enumeration)
- Web-Application may have some end-point that gives a list of all registered users.
- Advanced Search option sometimes gives all registered usernames.
- There can be some user-specific files (like profile picture), and Directory of those files has directory listing enabled. Then attacker will easily get all usernames without brute force.
Example 1: Enumeration using Forgot password page
Website http://site.com has forgotten password page.
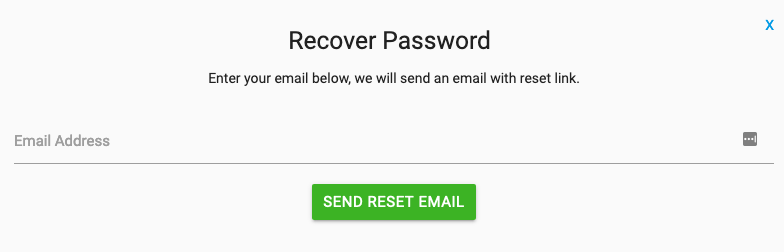
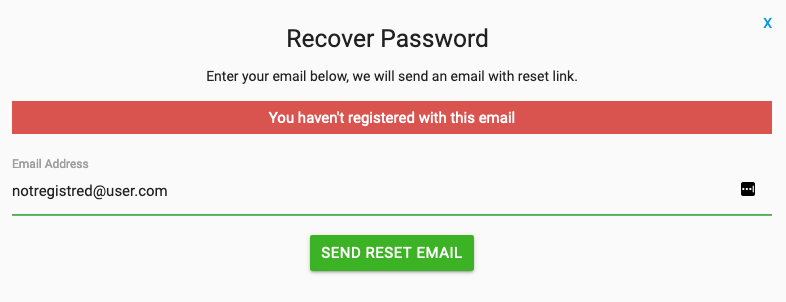
When I enter random email id and click on send reset email it will show error as,
Then, When I enter email which is registered on http://site.com it will show a success message as,
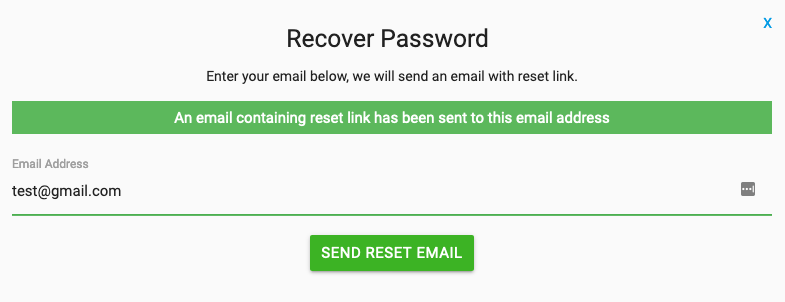
Thus, the attacker can enumerate registered email ids by brute force.
Note: This will send password reset mail to the actual user so that user will understand that someone tried to reset the password.
Example 2: Enumeration using Registration page
When we try to register to an account with email that is already registered, the Web application will show message something like
This email id already Registered.
But when we use a new email id in the same registration form, it will continue the registration process.
Thus, the attacker can enumerate registered email id's by brute force.
This method will not send any email to existing user which attacker tried to enumerate.
Impact
- Even though this vulnerability has no high impact, It can be used to get a list of usernames/emails, which further can be used to Takeover those accounts.
Prevention
- Only show generic error message or login, register and forgot password pages.
- Enable Rate limiting on these pages.
- Enable Captcha to block automated requests on Login, Register, Forgot password.
- Do not use sequential usernames, like user_101, user_102, user_103,...